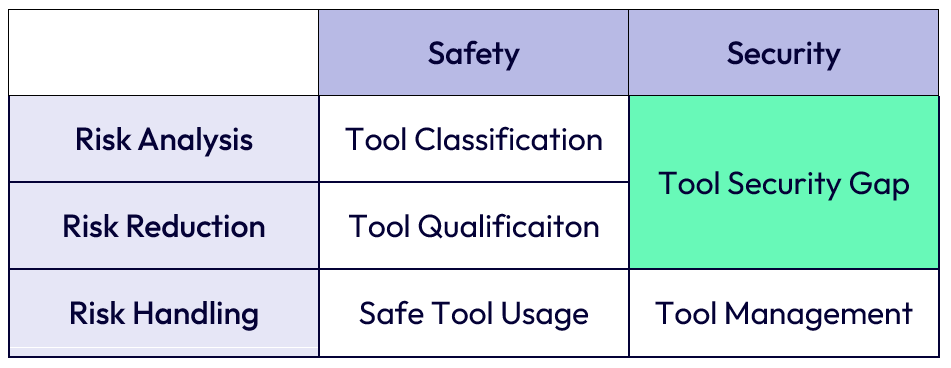
In the realm of functional safety, tool qualification is a structured process designed to provide objective evidence that a software tool is fit for developing safety-critical systems. Its purpose is clear: to ensure the tool neither introduces errors nor fails to detect them—errors that could jeopardize the safety of the final product.
Take the example of a compiler, a core tool that converts human-readable code into machine instructions. A subtle bug in the compiler could embed a hidden defect in the application—one that might surface only under rare conditions, yet with potentially catastrophic consequences. To mitigate this risk, qualification standards mandate a detailed analysis to establish the tool’s “confidence level” and define the steps required to prove its reliability.
The same principle applies to library qualification. Whether it’s a C++ standard library or an open-source component, these pre-built elements must be verified for their intended use. This step is critical because modern systems heavily depend on such libraries. A single flaw in a widely adopted library can propagate vulnerabilities across countless products.
For years, Validas has been a leader in this field, offering a model-based approach to tool and library qualification. Their methodology includes ready-to-use “Qualification Kits” (QKits), which automate much of the rigorous process. These kits deliver the necessary evidence and documentation, validated by certifying bodies like TÜV Süd, saving development teams significant time and enabling them to focus on their core innovations. This approach has proven to be an effective and indispensable strategy for managing safety risks.
 Deep Dive
Static Analysis for Safer C/C++: Avoiding Undefined Behavior and Closing Coverage Gaps
Deep Dive
Static Analysis for Safer C/C++: Avoiding Undefined Behavior and Closing Coverage Gaps
 News
Validas AG becomes Contributing Member of the Eclipse Foundation
News
Validas AG becomes Contributing Member of the Eclipse Foundation
 Deep Dive
The Tool Safety Manual: A Lifesaving Resource
Deep Dive
The Tool Safety Manual: A Lifesaving Resource